Which of the Following Are Useful Incident Analysis Resources
When investigations are not managed and documented properly processes fail critical items are overlooked inefficiencies develop and key indicators are missed all leading to increased. The program creates the Processor Scan Strings files depending on the current state of the system.

Explore Our Sample Of Cyber Security Incident Response Plan Template How To Plan Emergency Response Plan Business Plan Template
Incident handling teams may choose to build hash sets of known good operating system and application files so that they are better prepared to determine how the botnet has altered a system.

. Our industry experts share their top 10 tips for incident analysis from establishing the basics to leveraging results to assess manage and mitigate risk. Memory forensics database forensics network forensics etc. Incident handling hardware and software Laptops removable media forensic software digital cameras Incident analysis resources Documentation network diagramsbaselines critical file hash values Incident mitigation software - Clean OS and application images Policies needed for incident handling Everyone knows what to do.
Defining roles and responsibilities for performing incident management C. After gathering information use the facts to make a timeline of. It is an integral activity in the incident management.
Incident Documentation 16. The Incident Action Plan Safety Analysis ICS-215A is typically prepared by the Planning Section Chief during the incident action planning cycle. Resources must be inventoried and categorized.
Incident Notification Escalation. 200000 points QUESTION 2 1. Incident analysis resources include network diagrams and lists of ____ such as database servers.
Gathering physical evidence photos and videos from the scene of the incident if possible Interviewing the subject and victim if applicable and witnesses. Examples of resources include lists of contact and on-call information commonly used port numbers and known critical assets. Outlining a workflow for incident management activities E.
A relatively new approach created based on the lessons learned from the 911 terrorist attacks. Additional incident analysis resources might be required. ICS 200 Lesson 4.
Incident alerting takes place in this step although the timing may vary according to. Describes functional roles in resource management. The committees of the CPMT follow a set of general stages to develop their subordinate plans.
Formulating a Response Strategy 7. Resource management includes four key activities. Desk checks d.
Set yourself up to easily perform analyses and quickly generate reports. Removable media forensic software digital cameras etc. Documentation network diagrams critical file hash values C.
Incident analysis is a structured process for identifying what happened how and why it happened what can be done to reduce the risk of recurrence and make care safer and what was learned. The first step to incident analysis is to gather as many facts as you can as quickly as you can. Analyze manage and learn from patient safety incidents in any healthcare setting with the Canadian Incident Analysis Framework.
Defining interfaces between organizational components performing incident management B. Swimlanes can be used for the following. These files may or may not be present.
Examples of these resources are a list of critical assets network diagrams port lists hashes of critical files and baseline readings of system and network activity. Simulation software b. To avoid overburdening the incident command resources should not self-dispatch spontaneously deploy.
What is the goal of incident analysis. Overview of Data Collection Systems 62 This section provides an overall structure within which the different aspects of data collection and incident analysis methods can be integrated. Week 12 Assignment 1 Please answer the following questions.
Q2 Which of the following are useful incident analysis resources. What is incident analysis. There are several categories of dedicated incident response tools -- including vulnerability management SIEM network traffic analysis and data loss prevention -- that can provide information and analysis and create reports to help organizations prevent and respond appropriately to security attacks.
Provide examples of how resources are typed for various applications. Share security information enterprise-wide. Phones and contact information B.
A standardized approach to incident management that is applicable for use in all hazards. Notifying External Agencies 13. Describes the kinds of resources often used in incidents.
Security incidents and digital forensics investigations are complex events with many facets all of which must be managed in parallel to ensure efficiency and effectiveness. The Incident Command System ICS can be used to manage any type of incident including planned events. Protocol analyzers c.
The lack of filtering and aggregation at the individual server level causes larger amounts of data to be transferred over networks. Mitigation software is also an important item when preparing to handle a security incident. RALPRVD is the object file for the OSM Resource Layer Provider process which is used for initial discovery initial incident analysis event processing and all operations that require SUPER Group access.
A military system used in domestic incidents to ensure command and control of Federal resources. The goals of incident analysis are. Discusses how resources are procured.
Incident Analysis is a structured process for identifying what happened how and why it happened what can be done to reduce the risk of recurrence and make care safer and what was learned. NIMS Resource Management is important because in case an incident happens you need to get the right resources to the right place and at the right time in order to preserve the life and well being of the residents. This chapter is divided into the following sections.
Identifying and typing resources. Data Capture Incident Response Forensics tools is a broad category that covers all types of media eg. _____ is the release and return of resources that are no longer required and is a planned process.
The impor-tance of effective data collection systems as part of the continuous improve-. Track costs including losses and recoveries. Incident Resources 1 Lesson Overview The Incident Resources lesson.
They analyze the data from different log sources correlate events identify and prioritize significant events and initiate responses to events. Identifying handoffs of information during incident management D. Categorization is important to determining how incidents should be handled and for prioritizing response resources.
Communicating the Incident 5. Incident Response Forensics tools examine digital media with the aim of identifying preserving recovering analyzing and presenting facts and opinions about the digital information all designed to create a legal.

Root Cause Analysis Cause Mapping Basics Analysis Problem Solving Activities Business Process Mapping

Root Cause Analysis Template Report Template Project Management Templates Action Plan Template

Itil Templates Change Management Templates Service Level Agreement

Cyber Security Incident Response Cheat Sheet Behavior Analysis Cyber Security Analysis

Process Deviation Management Learning From Incidents Cge Risk

Incident Management It Process Wiki

Problem Analysis Templates 9 Free Ms Docs Xlsx Pdf Formats Samples Examples Analysis Report Template Business Analysis
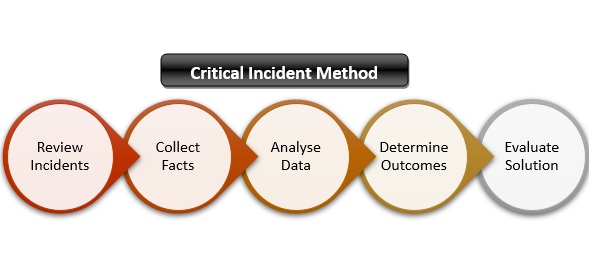
Critical Incident Method Meaning Importance Steps Example Mba Skool

No comments for "Which of the Following Are Useful Incident Analysis Resources"
Post a Comment